Social engineering: The chameleon effect
As cyberattacks continue evolving, hackers are using more advanced techniques like social engineering to target gaming ecosystems and their players. So how can you protect yourself against them?

As cyberattacks continue evolving, hackers are using more advanced techniques like social engineering to target gaming ecosystems and their players. So how can you protect yourself against them?

Among the growing arsenal of attacks, one method has emerged as a popular threat: social engineering.
This article will delve into some of the common social engineering attacks relevant to the gaming ecosystem and how you can build robust defenses to protect against them.
A big cyber risk for organizations isn’t a fancy hacking attempt. Many attacks take place leveraging an ancient trap: human deception, or ‘social engineering’ in security terms. Social Engineering heavily depends on capitalizing on the users’ weaknesses and misfortune.
Social engineering allows cybercriminals to manipulate victims into sharing confidential information. Unlike traditional malware attacks, social engineering exploits human vulnerability, bypassing technological barriers and making detection harder.
Leveraging human psychology, attackers prey on trust, empathy, and curiosity, pretending to be somebody else to persuade a person to act. For example, player support agents may be approached by bad actors to acquire valuable information, which is later used to steal accounts.
You have likely received phishing attempts disguised as banks or phone companies in the past. The gaming industry is no different, with bad actors getting more creative every day.
According to Eftsure research, the average organization faces as many as 700 social engineering threats annually.
Those numbers uncover an alarming truth – the average organization is quietly under siege, being targeted by nearly two social engineering attacks every day!
Player support agents are frequently approached by bad actors impersonating players or other agents, aiming to acquire information for malicious purposes, like obtaining account details and in-game currency within the gaming ecosystem.
Let’s explore some common social engineering methods:
Phishing involves sending deceptive emails or messages to players, appearing to be from reputable sources like support agents or other players.
The goal is to trick recipients into providing personal or valuable information, like passwords, credit card details, or digital in-game assets.
Phishing can also be a starting point for larger cyber-attacks, as it helps gather information on the target and establishes an attack vector.
In this technique, the social engineer first gains the trust of the target person–like a player or support agent–and then requests help or assistance.
By building a relationship, the attacker can manipulate the player or agent into revealing sensitive information, like account details, financial information, or access to restricted systems.
This form of social engineering often occurs when bad actors approach agents through social media, pretending to be coworkers.
Pretexting involves creating a false scenario or tricking someone into providing sensitive information or performing actions.
For example, players may be approached by bad actors impersonating help desk agents, asking for credentials to perform an attack.
Social engineers may impersonate authority figures, like company executives, managers, or team leads, to gain trust and convince individuals to comply with their requests.
They exploit the inherent trust people have in these positions to deceive and manipulate their targets.
In some cases, bad actors with access to company IT resources use internal email accounts to make their impersonations more credible.
When it comes to cyber risks, it’s important to realize that you will never be 100% secure and protected against social engineering – but you can minimize the risk.
Preventing social engineering requires a combination of awareness, vigilance, and good security practices built on the right combination of technology, processes, and people’s behavioral aspects in an integrated approach.
With this approach in mind, you can take the following measures:
Safeguard your digital fortresses:
Keep your systems and applications up to date with the latest patches and security fixes.
Enable automatic updates whenever possible to ensure you are protected against known vulnerabilities.
Deploy security monitoring and phishing detection.
Perform security assessments, including simulated phishing campaigns and social engineering tests, to identify vulnerabilities and areas for improvement.
Encrypt communications, with extra care for confidential information.
Use a virtual private network (VPN) for secure connections.
Build robust protection processes:
Use strong and unique passwords and password managers to generate and store complex passwords.
Enable multi-factor authentication (MFA) to add an extra layer of security beyond passwords.
Regularly review and update access controls, ensuring that users only have the permissions necessary for their roles and responsibilities.
Verify the identity of individuals who request sensitive information or access to restricted areas, even if they claim to be colleagues or service providers.
Empower your human firewall:
Educate your teams about different types of social engineering attacks and the tactics used by attackers.
Conduct regular security awareness training for employees to reinforce best practices and educate them about evolving social engineering techniques.
Encourage open communication about potential threats and develop a healthy skepticism.
Question requests for sensitive information or actions that seem unusual or out of the ordinary.
Avoid sharing personal or sensitive information via phone, email, or social media unless you have verified the legitimacy of the request.
Taking an integrated approach based on the proven NIST Cyber Security Framework, is essential. First of all, prevention by protection is important, but so is the ability to forecast and detect risks early, responding adequately, and recovering as soon as possible.
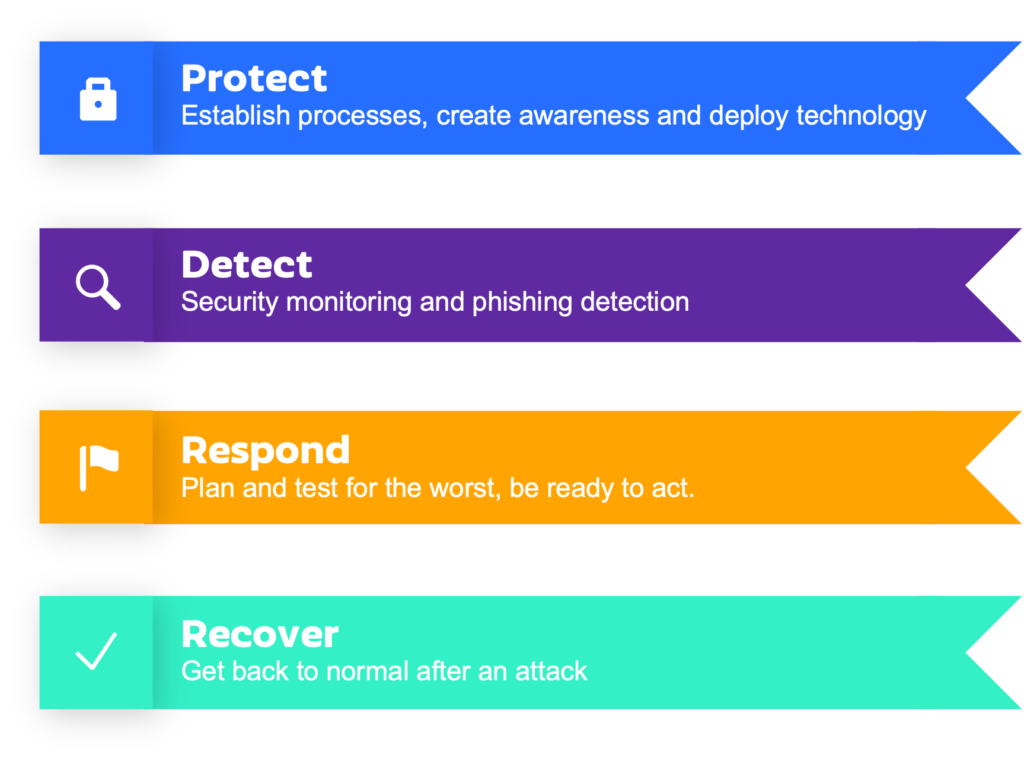
Social engineering is a significant challenge within the gaming industry, threatening the integrity of player experiences. With social engineering attacks constantly evolving, you need to stay updated on the latest tactics and techniques used by attackers.
By combining technology, people, and behavioral aspects with strong processes and security practices, you can significantly reduce the risk of falling victim to social engineering.
By taking the measures described above, you can significantly reduce the risk and continue to improve the safe and secure environment needed.
At 5CA, we have a unified Microsoft Platform Foundation, ensuring a safe and secure gaming environment for your players and safeguarding gaming etiquette. Our support services allow in-game content moderation, fraud management, and actionable insights that allow you to detect problem behavior proactively.
If you want to learn more, get in touch.
David Bos is an avid gamer with over 23 years of experience in serving global customers. Currently serving as CTO at 5CA, former Deloitte CTO and technology leader. Bos is also a part-time Lecturer on Data & AI and Cyber Security at Amsterdam University.
His specialties lie in technology, innovation, data & AI, automation, and cyber security.

What’s really keeping customer experience (CX) leaders in the gaming industry awake at night? Against the backdrop of rapidly advancing technology, it’s the enduring operational challenges that stand out significantly.

In the fast-paced world of online gaming, the terrain is shifting under our feet with every passing quarter. We are seeing seismic changes in how games are marketed, how players are retained, and, importantly, how Player Support is evolving.